Hi KevinTheJedi
I upgraded php to 7.2, activating all required php extensions on the latest Osticket version:
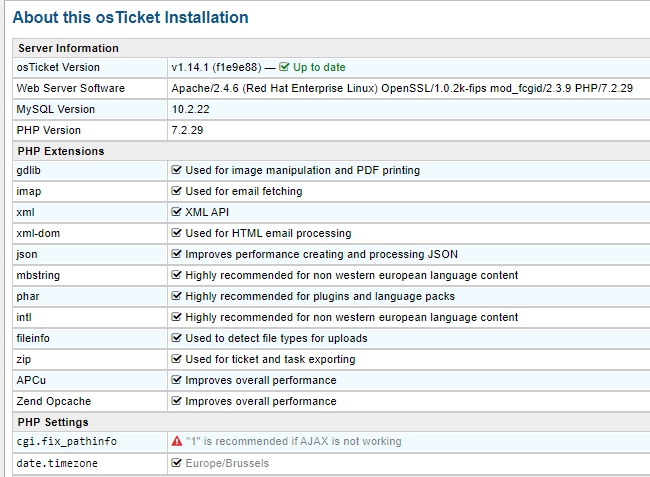
I didn't care about cgi.fix_pathinfo setting because I saw that it shouldn't be blocking.
I managed to test LDAP connection from command line, from CLI both search and authentication are working as they should. Here you can see a successful login attempt followed by an attempt with invalid credentials.
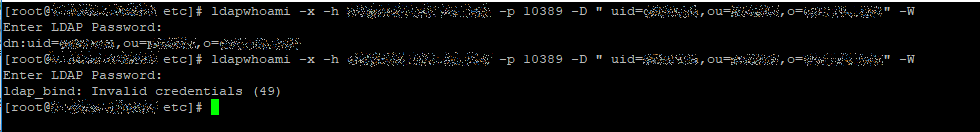
Nevertheless, when Osticket is trying to connect to the same port of the same server, it cannot bind the Ldap server:
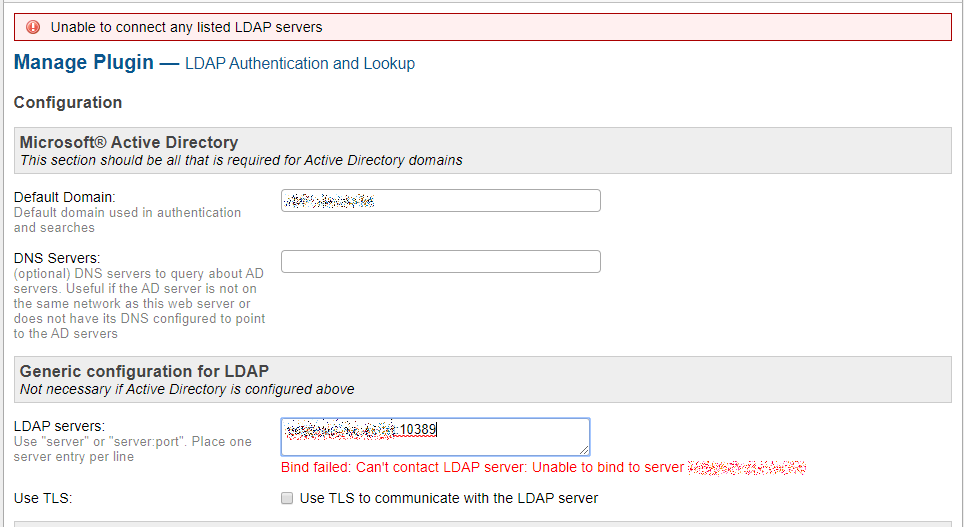
So apparently I can manage to authenticate from command line, excluding firewall block, invalid credentials or invalid search base, but Osticket cannot manage to authenticate.
When I try to login, the following error is generated in the apache error log, which makes me think that the plugin still needs some fix to be used with a port specification after the server name:
[Sun Mar 22 02:22:22.337494 2020] [php7:error] [pid 61823] [client <CLIENT_IP>:49221] PHP Fatal error: Uncaught Error: Call to a member function rootDse() on null in phar:///var/www/html/osticket/include/plugins/auth-ldap.phar/authentication.php:262\nStack trace:\n#0 phar:///var/www/html/osticket/include/plugins/auth-ldap.phar/authentication.php(193): LDAPAuthentication->getSchema(NULL)\n#1 phar:///var/www/html/osticket/include/plugins/auth-ldap.phar/authentication.php(430): LDAPAuthentication->authenticate('USERNAME', 'PASSWORD')\n#2 /var/www/html/osticket/include/class.auth.php(235): StaffLDAPAuthentication->authenticate('USERNAME', 'PASSWORD')\n#3 /var/www/html/osticket/scp/login.php(72): AuthenticationBackend::process('USERNAME', 'PASSWORD', Array)\n#4 {main}\n thrown in phar:///var/www/html/osticket/include/plugins/auth-ldap.phar/authentication.php on line 262, referer: http://<SERVER_FQDN>/scp/login.php