softaculous @ntozier so, still working though this issue with my institution cPanel admins and support. We've got the plugin working (not defunct missing, can access settings for the plugin) in our dev environment, but we're still trying to figure out how the hell we actually got there since it just turned up that way when I came back to work after the weekend.
My hunch (considering the installations at this point are identical between our dev and prod environments) is that it's a service running on the server causing this issue.
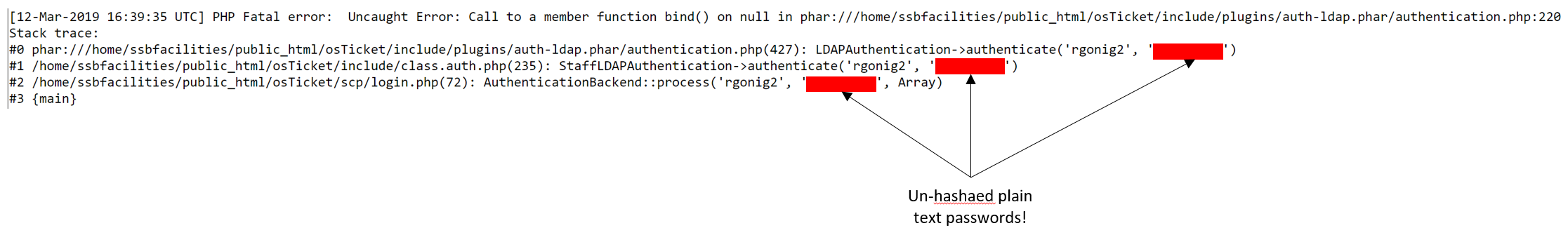
However, in attempting to debug, we found another issue which may warrant it's own request in Git. When the plugin is installed correctly, but configuration (bind details, account credentials, etc...) and a user who is set to be authenticated through the plugin attempts to login, raw user credentials are present in the stack trace error generated (only occurs PHP 7.1 and up, as lower PHP versions do not include stack trace in error logs):