It’s likely one of two things:
- Attributes not correct.
- The user is locked into LDAP so you must login to the database, go to the user_account table, and set the
backendvalue to NULL for the affected user(s).
Cheers.
It’s likely one of two things:
backend value to NULL for the affected user(s).Cheers.
Please let us know if either of those suggestions resolve your issue.
If they do not then you will want to post screen shots of your plugin and m365 settings.
Thanks for reply and follow-up but issue is not resolved. Please find attached plugin configuration of O365. When i tried to login with O365 ID, after authentication log in session is not establishing.
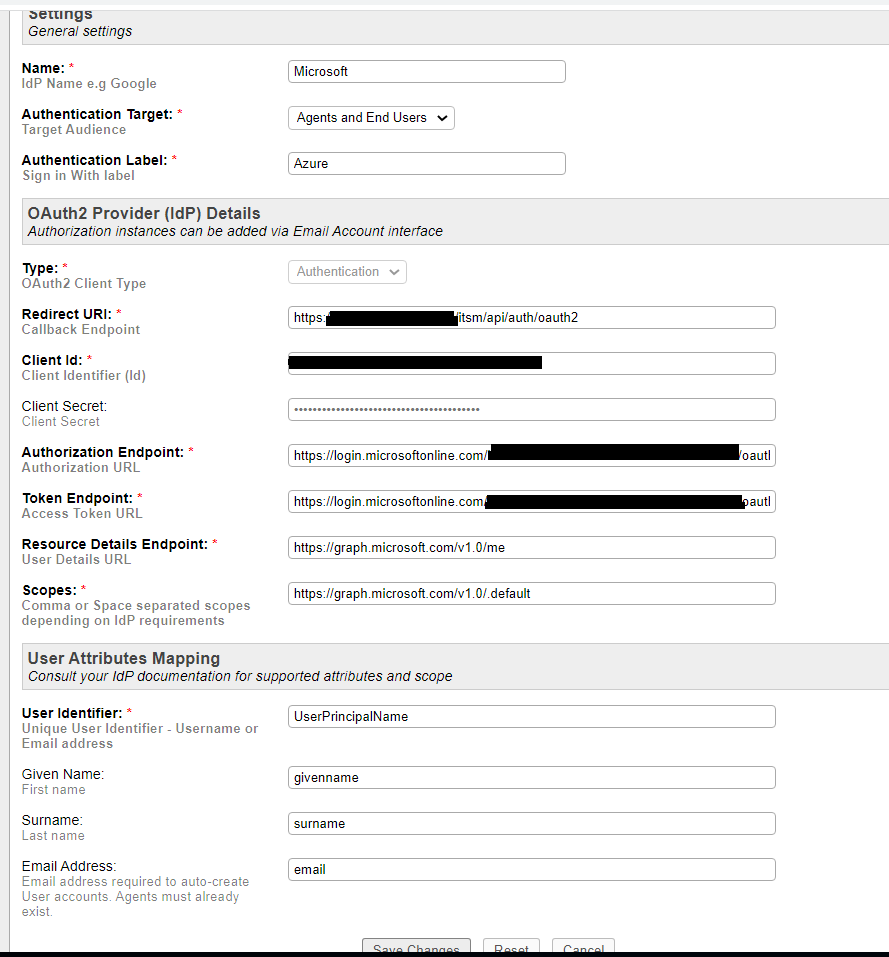
I'd assume your attributes don't match. Try using email for the User Identifier. Also, when you added the Client Secret did you use the Client Secret Value or the Client Secret ID? You should be using the Client Secret Value. Also, the Client ID should be the Application (client) ID from the App Registration.
Cheers.
@Mukund81 you can install SAML, WS-Federation and OAuth 2.0 tracer - (https://chrome[dot]google[dot]com/webstore/detail/saml-ws-federation-and-oa/hkodokikbjolckghdnljbkbhacbhpnkb?hl=en) in order to record the OAuth2 flow and see what user attributes are sent by Azure and its names.
Make sure you are registering at the User Mapping section the right names and also make sure Azure is providing all required attributes.
KevinTheJedi
I have tried with email as user identifier but get same issue. Also used Client secret value, not secret id. and client ID is also application id from app registration.
sixtomarttin
Please find attached trace output.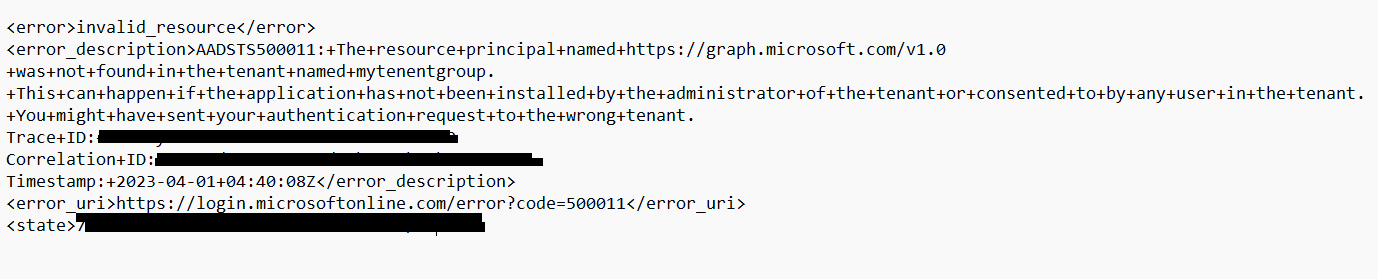
Getting same error after configuring shared attributes.
Then maybe the user/agent is locked into a specific authentication method. Go to the database. Go to the user_account or staff table. Then check the value of the backend column. If this is set to something then they are locked into that provider. You can clear out the value (make it empty) to allow them to login using any authentication method.
Cheers.