I have osTicket 1.14.2 running on an external website, outside of our domain, and am trying (like many before me) to authenticate via LDAP to our in-house Active Directory.
This is the config of my osTicket server:
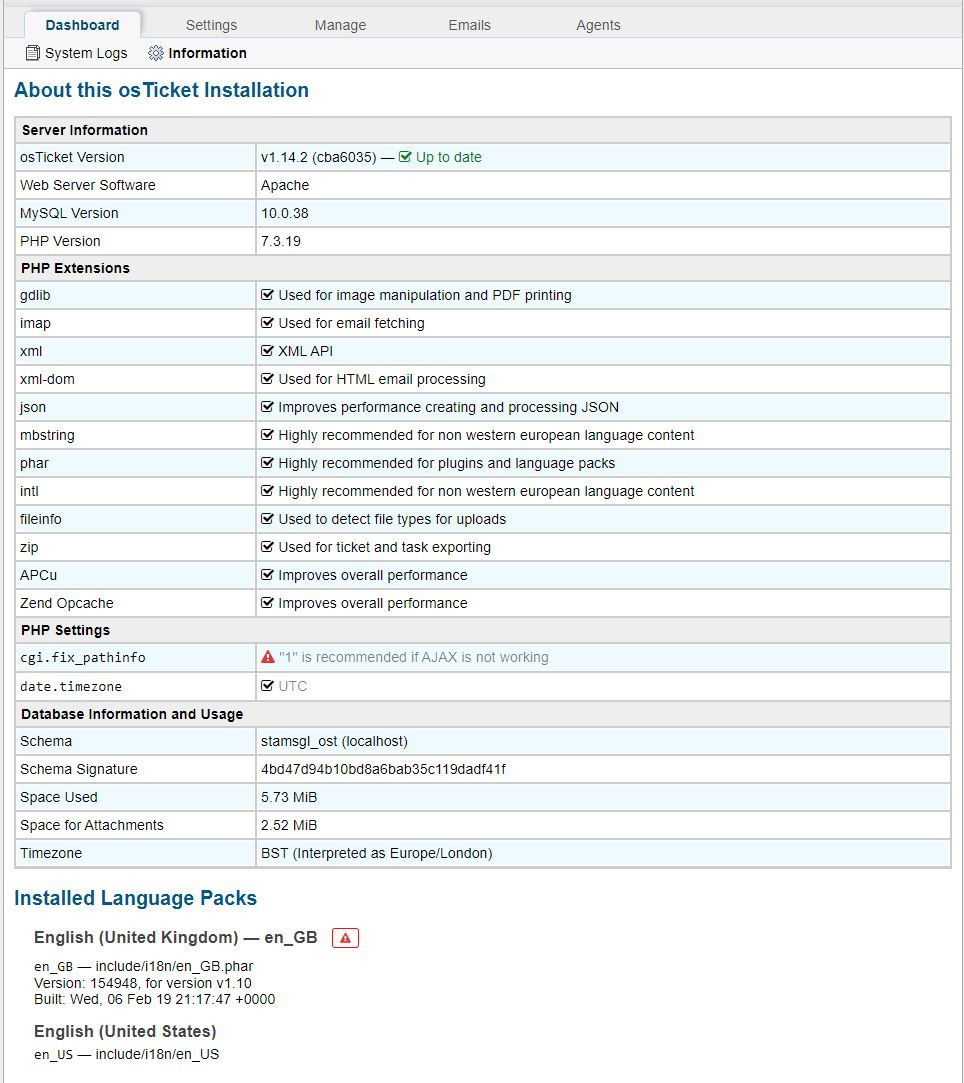
And this is my LDAP plugin page:
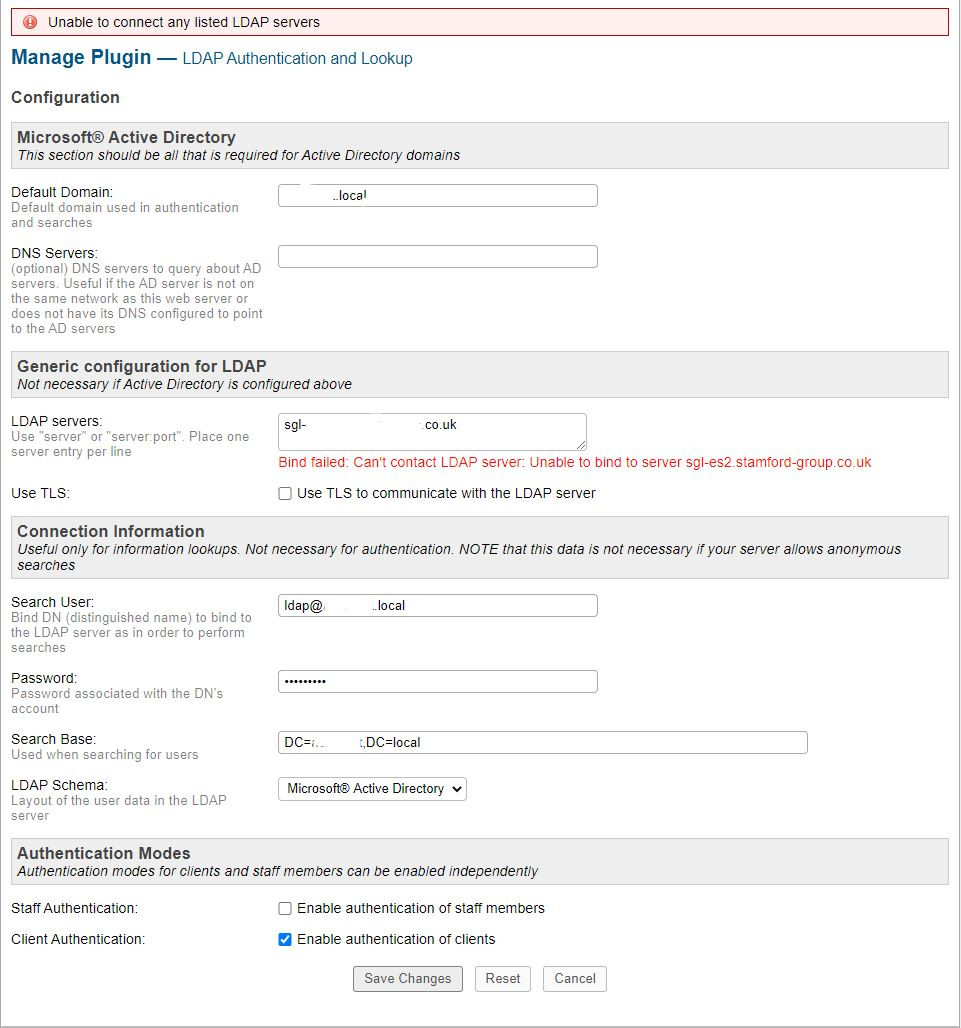
I am vaguely aware that the php version might be an issue, but I have tried setting the server to differing versions from 5.4 upwards, same effect, Bind failed.
I have tested using the utility LDAP Admin from my home PC, that my username and password are correct, it fails if I try to use SSL or TLS as the server in question doesn't have an external SSL certificate configured in Certificates - Service (Active Directory Domain Services), so prompts with an unverified certificate error, so I understand that's not going to work, but accessing non-secure port 389 authenticates from my home machine fine.
If I remove the .phar plugin and use the auth-ldap/ files from Github, I get a server error 500 when I try to submit my settings. edit apparently I needed the include folder for LDAP2 stuff from the existing .phar to fix that, but the version from github is 0.6.2 compared to 0.6.3 from the osTicket download, so presumably is out of date anyway.