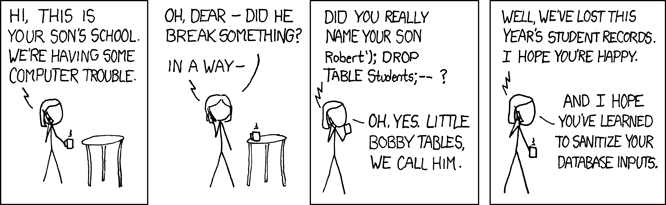
I'd like to call attention to a security vulnerability that would be important to address. I noticed this when I edited a new form and made a custom "choices" list. In the "choices" config I put in a value that contained "<" and ">". When I previewed my form, I noticed that this broke the form. The form being broken is a mild concern - take out the html tag chars ">" and "<" and the form works just fine. But that called to my attention that OSTicket is taking the input from a use and not sanitizing the input and just using it directly. This is a security issue. It means that I can just close the tag of the code for the input box that I'm typing in and inject my own code. This is especially dangerous if that input is stored in a database and persistently displayed in the system and not just used during the life of the current session. Attached is a comic strip that outlines the problem in a humorous way.Risks include (but not limited to):SQL injection, code injection, cross site scripting, etc...This was the same vulnerability that caused the infamous myspace worm that propagated to millions of users in a few hours. It is also the most commonly found security vulnerability on the web.