That's exactly what I thought too after upgrading to osTicket 1.17 and seeing that unencrypted 143 failed.
So I tried with 993, installed the certificate from our own internal certificate authority, but:
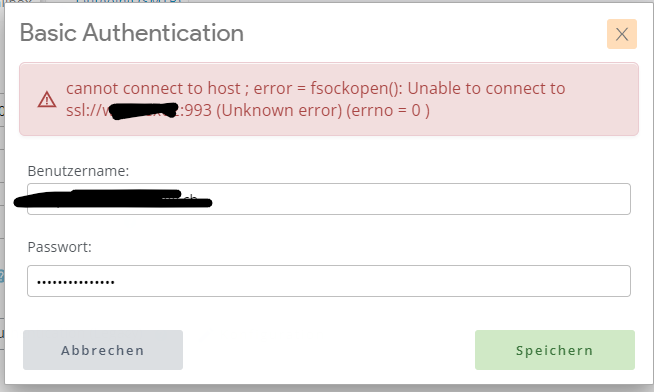
We tried adding a ssl:// or tls:// in front of the servername. Didn't help.
Tried reissueing the certificate from target server, didn't help.(Also making sure the is no mismatch in CN etc.)
Tried installing the certificate in any of the available folder in Windows Computer Certificates, didn't help.
CA certificate is installed.
Firewall isn't blocking according to logs. Port is accepted. Can reach the target server through other protocols.
We are using IIS(unfortunately we have to).
Is osTicket using openssl, so using a selfsigned certificate will not work as openssl doesnt use the windows certificate store?
Checking the connection with "openssl s_client -connect server:993" will fail with "unable to get local issuer certificate" which as I understand is normal. Because it doesnt know about my self signed certificate in the windows computer certificates.
I will try to put all 3 certificates I need into a single .pem, so I can use curl.cainfo in php.ini to make the certificates available. But this is not really helpful as no one in my company will be able to manage this when certificate are out of date.
Sorry for the long post.
Regards